What is the NIST Cyber Security Framework?
Background
The NIST Cyber Security Framework was initially established in 2013 as the result of a US Executive Order introduced to build a successful cyber security framework to protect critical infrastructure. It is now accepted as a general cyber security framework, that can be tailored to organisations in any industry.
The framework continues to be developed alongside government stakeholders, industry experts and academics.
The Framework provides a common language and methodology for businesses to;
- Appraise their current cybersecurity posture;
- Describe their target state of cybersecurity;
- Identify areas of continual and reproducible improvement;
- Evaluate progress towards their target state;
- Communicate cyber security risk to internal and external stakeholders
The Framework Core
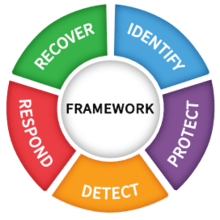
“These five Functions were selected because they represent the five primary pillars for a successful and holistic cybersecurity program.” - National Institute of Standards and Technology (NIST)
At its highest level, the core of the framework resides in its ‘Five Functions’:
• Identify the assets and processes that need to be protected
• Protect your organization, its information, and digital assets, by implementing technical controls designed to prevent attacks
• Detect dangerous and anomalous activity, whether this is internal or external. Knowledge is power, and if you know what attention your organization is attracting, you can better protect and respond against it.
• Respond to any suspected or actual cyber-attacks or information security incidents. Quick and thorough action, on-time, every time, is essential.
• Recover from cyber and information security incidents quickly and robustly, rebuild stronger and minimize any disruption to business operations.
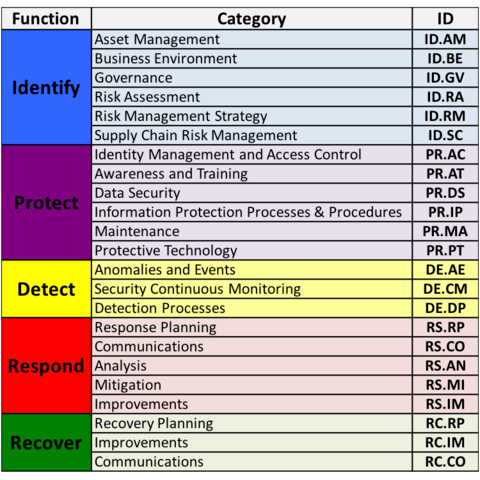
At the next level down, these five functions are divided into 23 categories:
These categories were designed to cover the entire breadth of cyber security risk management.
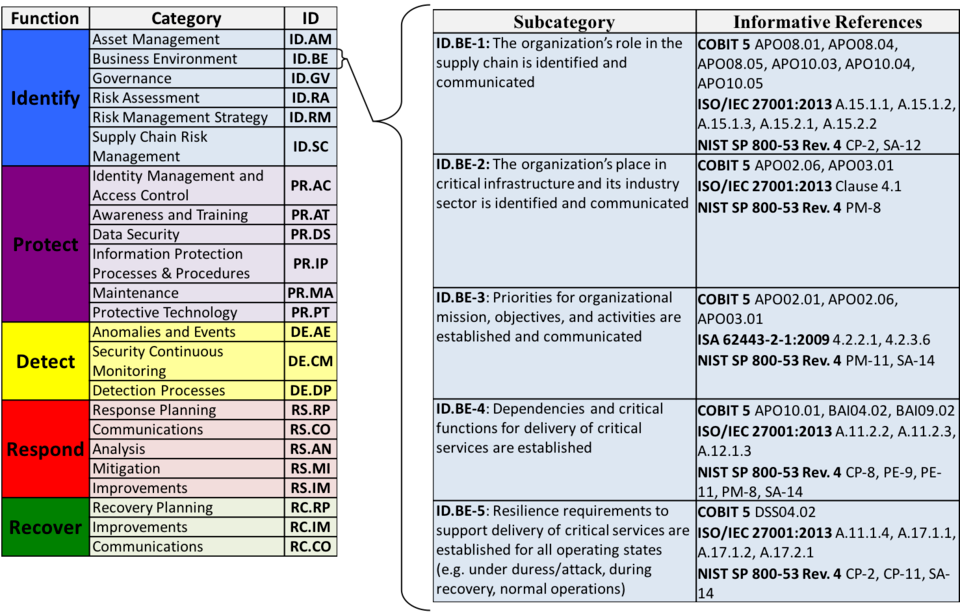
At the deepest layer of the core - these categories are further divided into 108 subcategories:
Each subcategory includes corresponding informative references - documentation that can provide further technical guidance and assistance on achieving the goals outline by each subcategory.