Guide to the Risk Assessment Module
How to Perform a Cyber Security Risk Assessment with HighGround
Table of Contents
Why Perform a Cyber Security Risk Assessment?Getting Started with Risk AssessmentsHow to Perform a Risk AssessmentView your Risk Assessments:Risk Assessment Status'How-To Guides:Why Perform a Cyber Security Risk Assessment?
Risk Assessments (RA) are a vital component of your cyber security defence to identify your risks and gaps with your cyber security.
In order to protect your organisation against threats and minimise risks, you first need to Identify what they and what the likelihood and impact of these may be. After all, you can't start strengthening your weaknesses if you don't know what they are. This is the knowledge that is gained from performing a Cyber Risk Assessment - knowledge which can then be turned into actionable intelligence so that you can begin securing, reducing and eliminating those risks and to develop response and recovery capabilities.
Cyber Security is often misunderstood and considered to be an 'IT problem' despite it being a major business risk in its own right with devastating consequences when it goes wrong. By failing to recognise cyber security as a risk and managing it as such, many businesses are mismanaging their cyber security. Another benefit of performing a Cyber Risk Assessment is that you can present cyber security to the Board as a business risk and not an IT problem, in a meaningful and understandable format that the Board can understand in the context of the businesses operations, objectives and risks.
Getting Started with Risk Assessments
Free Resources
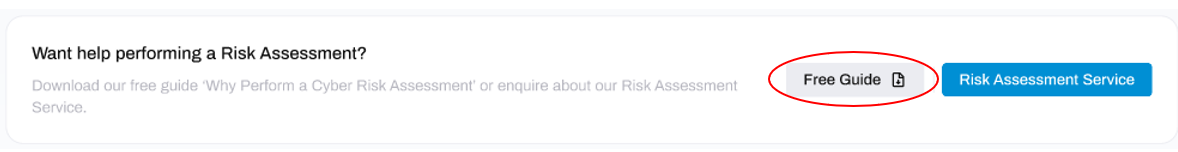
To help you get started, we provide a free guide on Cyber Risk Assessments which can be accessed by clicking on the Free Guide button located near the top of the window.
DeleteProfessional Assistance
Our Cyber Risk Assessments are aligned with the NIST Cyber Security Framework, ISO 27001, Cyber Essentials Plus and CIS Controls. When used together with our Vulnerability Assessments, you will gain a detailed and actionable understanding of your current Cyber Risk Posture.
Packages:
-
Basic: our basic package offers an entry level, Level-1 Risk Assessment which involves working through a 30-45 minute session with one of our business analysts on a structured questionnaire with a report provided to you at the end.
- Advanced: our advanced package offers an extensive, comprehensive Risk Assessment working with our business analysts, senior security engineers and your C-Suite and IT department/provider covering 16 key sections and over 168 questions, laser-focussed on your current cyber security risk in relation to the business context and overall risk landscape - producing a detailed and thorough report of your risks at the end.
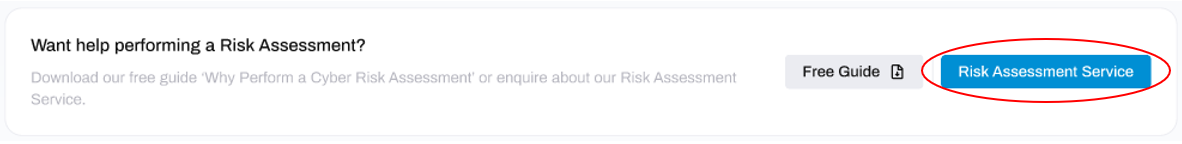
To find out more, make an enquiry, or purchase a package - click the Risk Assessment Service button located toward the top-right of the window.
This will trigger a slide-out window from the right hand side of your screen:
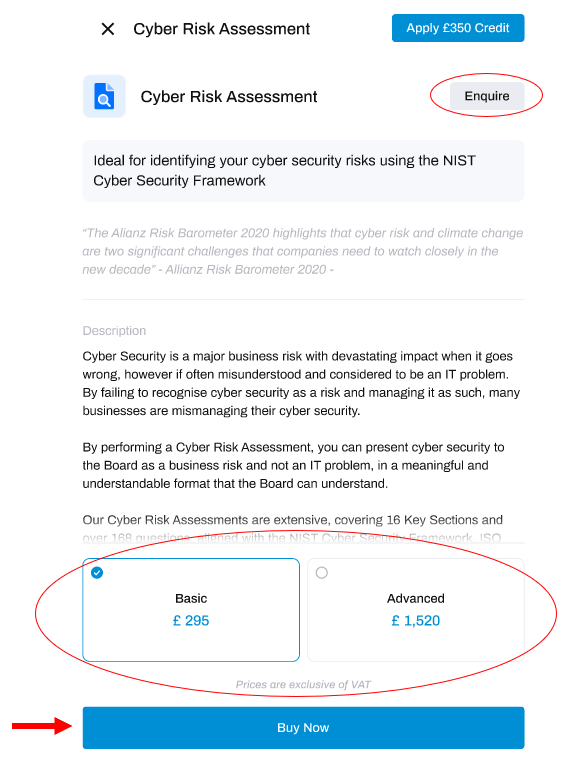
Here you can make an enquiry by clicking the Enquire button if you prefer to speak with our sales team first, or choose your package and click the Buy Now button to purchase this service.
How to Perform a Risk Assessment
To make it easy for you, we provide a pre-written Risk Assessment template created by our expert cyber security team, ready for you to use. To get started, follow the steps below:
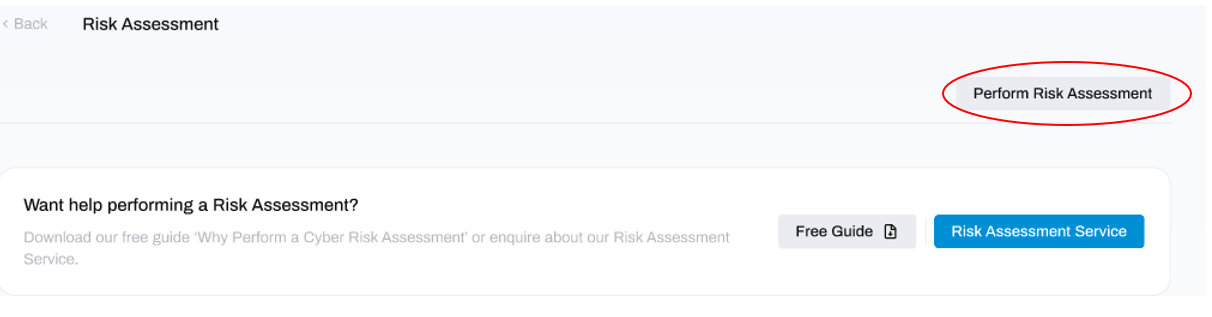
STEP 1: Click Perform Risk Assessment Button
Click the Perform Risk Assessment button located at the top-right of the Risk Assessment module:
This will open a new window containing the Risk Assessment questions.
STEP 2: Answer the Questions
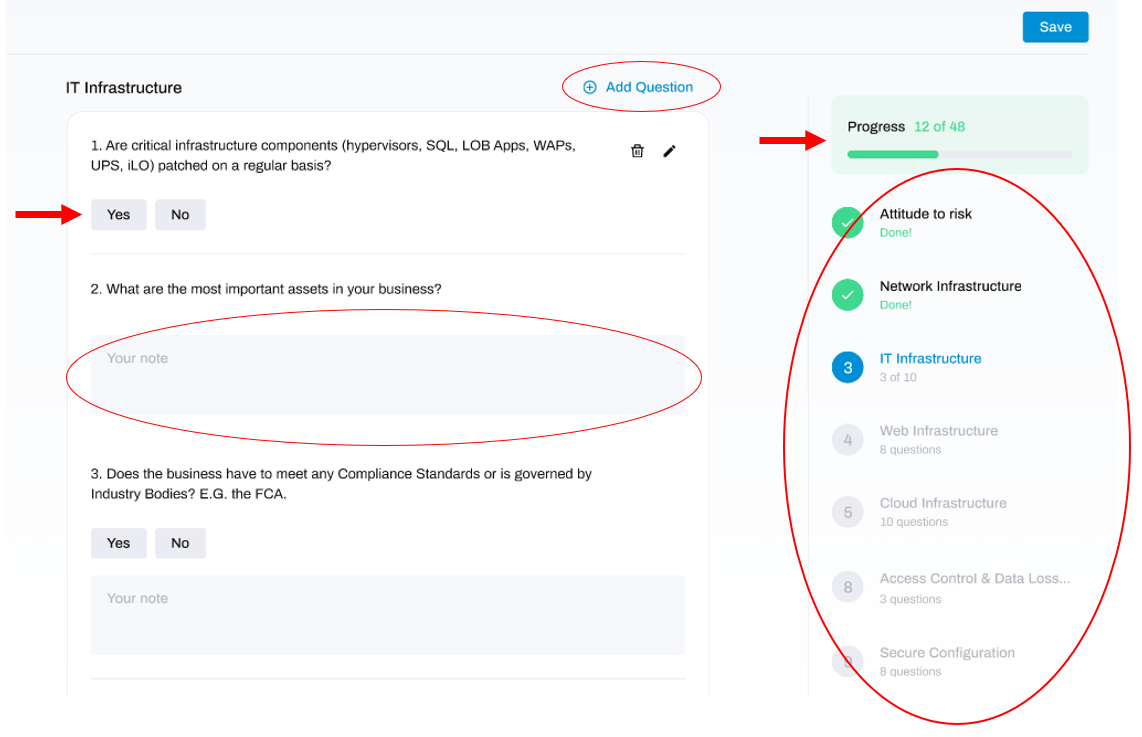
- To perform the Risk Assessment you will need to answer all of the questions in each section of the Assessment.
- Read through each question carefully and perform any actions/checks required to answer the question.
- Afterwards, select a Yes or No answer and/or type the answer in the notes box.
You can keep track of your progress by viewing the pane at the right-hand side of the Assessment window. Blue circles containing a number indicate that a section has not been started yet. If you are currently completing or have completed a section fully, there will be a green tick displayed next to it. If you have moved past that section without completing all questions, there will be an orange tick displayed next to it. The progress bar at the top will show you the number of sections you have completed.
Add a Question
If you want to add your own question to the Risk Assessment, click the Add Question button located towards the top-right of the window.
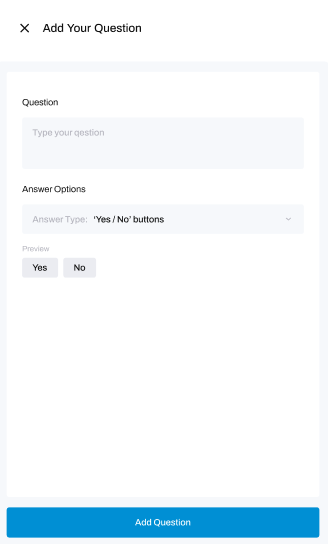
This will open another window where you can compose your question, and select the answer type:
Answer options can be in the form of Yes/No buttons, a Note field (for typing answers) or a Date/Time.
After filling in those details, click the Add Question button.
And that's it! Your question has been added.
STEP 3: Finish and Save
Once you have answered all the questions, click the Save button located at the top-right of the window:
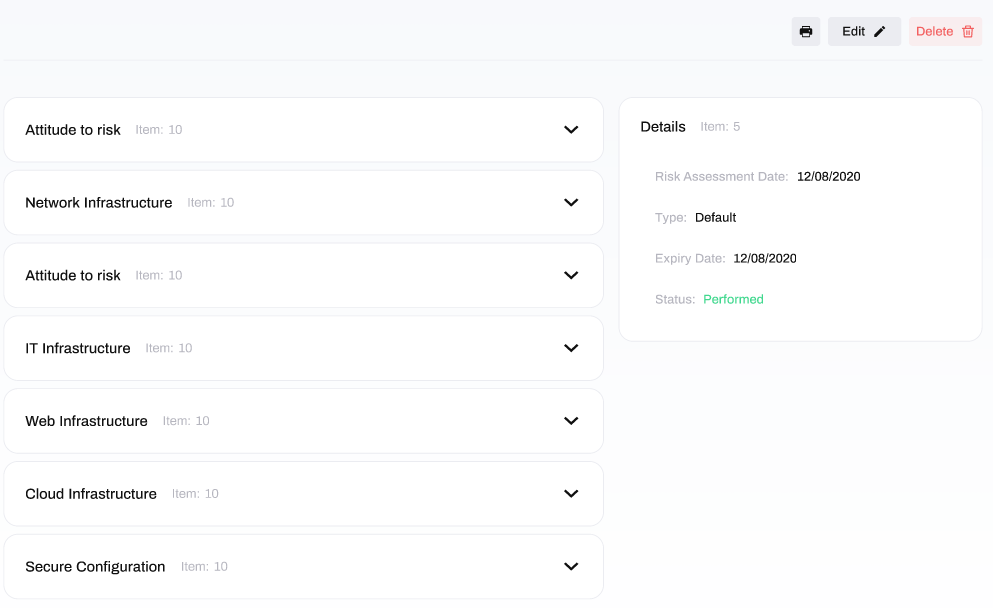
And that's it! You have completed the Risk Assessment.
DeleteView your Risk Assessments:
At the bottom of the Risk Assessment module you can view your previous Risk Assessments:
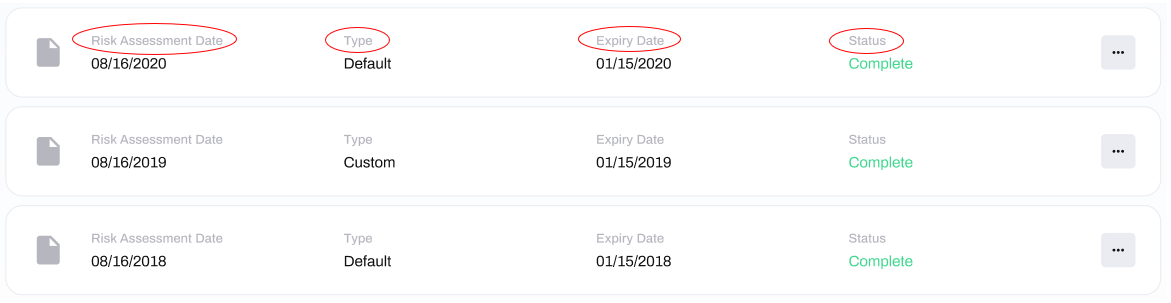
The columns display the following information:
- Risk Assessment Date: the date that the Risk Assessment was performed.
-
Type:
- Default - the Risk Assessment contains only the pre-written, default questions.
- Custom - the questions in the Risk Assessment have been modified, and/or new questions have been added.
- Expiry Date: when the Risk Assessment will expire, this will be a year after it was performed.
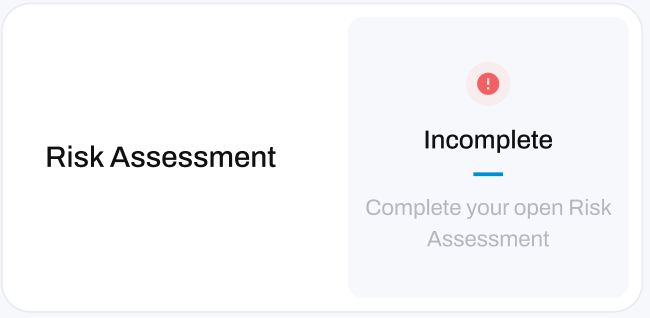
- Status: whether the Risk Assessment was Completed, or is Incomplete.
Compliance Status'
In order to stay up-to-date and aware of your cyber security risks, you should conduct a Risk Assessment twice yearly. The Compliance Status' are designed with this in mind, and will keep you informed on the state of your risk awareness.
To learn more about what your status means, choose the matching icon from the tabs below:
Status' in a default state appear as a blue cross, and indicate that you have never conducted a cyber security Risk Assessment.
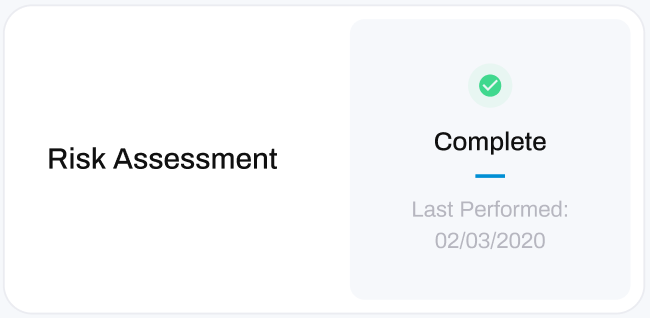
DeleteStatus' in a healthy state appear with a green tick with a status of Complete.
- This status indicates that you have completed a Risk Assessment within the last 6 months.
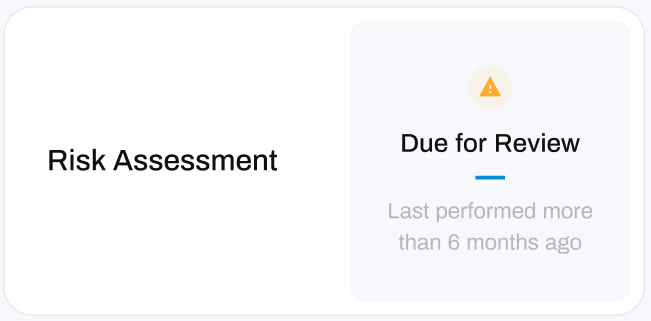
Status' in a warning state will show with an orange exclamation mark with a status of Due for Review.
- This status indicates that your last Risk Assessment was completed more than 6 months ago.
How-To Guides:
Perform a Risk Assessment
To make it easy for you, we provide a pre-written Risk Assessment template created by our expert cyber security team, ready for you to use. To get started, follow the steps below:
STEP 1: Click Perform Risk Assessment Button
Click the Perform Risk Assessment button located at the top-right of the Risk Assessment module:
This will open a new window containing the Risk Assessment questions.
STEP 2: Answer the Questions
- To perform the Risk Assessment you will need to answer all of the questions in each section of the Assessment.
- Read through each question carefully and perform any actions/checks required to answer the question.
- Afterwards, select a Yes or No answer and/or type the answer in the notes box.
You can keep track of your progress by viewing the pane at the right-hand side of the Assessment window. Blue circles containing a number indicate that a section has not been started yet. If you are currently completing or have completed a section fully, there will be a green tick displayed next to it. If you have moved past that section without completing all questions, there will be an orange tick displayed next to it. The progress bar at the top will show you the number of sections you have completed.
Add a Question
If you want to add your own question to the Risk Assessment, click the Add Question button located towards the top-right of the window.
This will open another window where you can compose your question, and select the answer type:
Answer options can be in the form of Yes/No buttons, a Note field (for typing answers) or a Date/Time.
After filling in those details, click the Add Question button.
And that's it! Your question has been added.
STEP 3: Finish and Save
Once you have answered all the questions, click the Save button located at the top-right of the window:

And that's it! You have completed the Risk Assessment.
Delete Risk Assessment
To delete a Risk Assessment, click the three dots to the right of the Risk Assessment that you want to delete, and click the Delete option.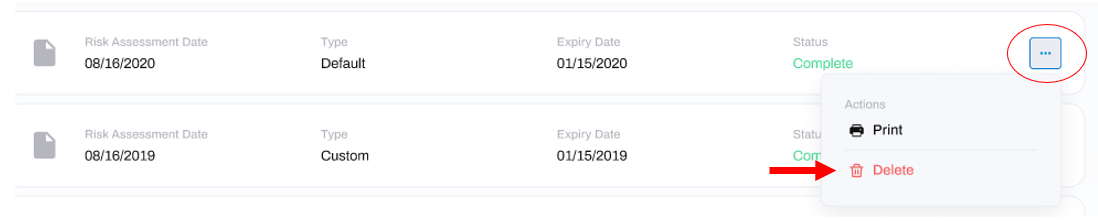
That's it! You've deleted the Risk Assessment.
Edit or Delete a Question in your Risk Assessment
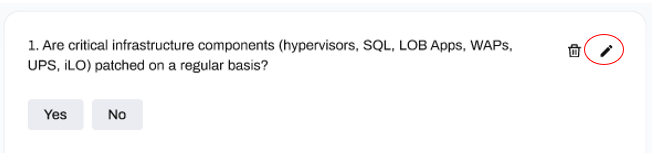
Edit Question:
To edit a question, click the pencil icon next the question you would like to edit:
This will make the question editable:
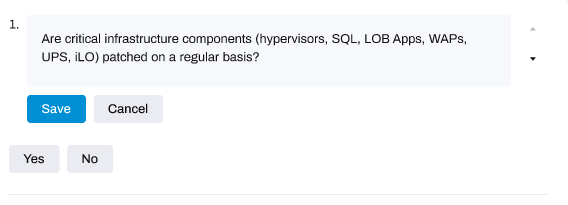
Remember to click the Save button after to keep your changes.
Delete a Question:
To delete a question from the Risk Assessment, click the bin icon next the question you would like to delete:
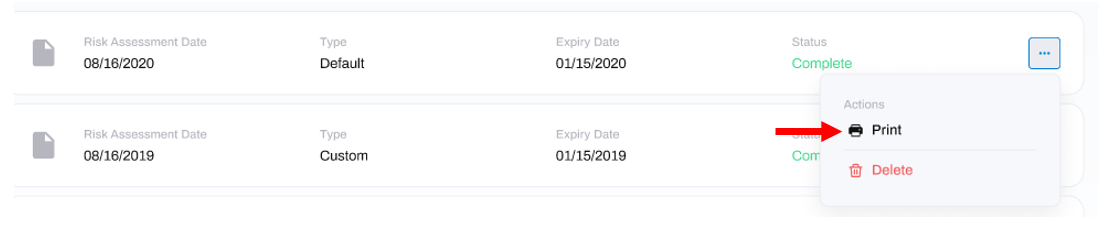
Print Risk Assessment
To print a Risk Assessment, click the three dots to the right of the Risk Assessment that you want to print, and click the print option:
This will trigger a file download either in a new tab or as a download, depending on your browser settings.